RKhunter Notes
Overview
Rootkit Hunter (rkhunter) is a security monitoring tool. It scans for root kits and other basic vulnerabilities. To be effective it needs to be run on a system initially known to be in a good state, and then have ts properties updated after every system update.
Installation
As is common for me, I have created a SaltStack state to install, configure and maintain rkhunter across all our network nodes. While I initially was maintaining different config files for each type of whitelist I needed to enable, it quicckly becaime unwieldym so new machines have all the witelist items added to the machine specfic scriptwhitelist.conf file. Once I go back through the earlier install machines the below can be greatly simplified.
# Installs rkhunter forensic tool
# Created: 2022-12-18
# Tested on Gentoo Linux
# Modified to work on Manjaro-ARM too 2023-01-02
#
{% set polaris = 'rkhunter' %}
# rkhunter is a forensics root kit hunter *nix like operating systems
# Before first use rkhunter --propupd to update properties database.
# Tocheck system rkhunter --check --sk
# To check config rkhunter --config-check
# Config file /etc/rkhunter.conf
#
{% if ((grains['os'] == 'Gentoo') or (grains['os'] == 'Manjaro-ARM') or (grains['os_family'] == 'Arch') or (grains['os_family'] == 'Debian')) %}
{% if grains['os'] != 'Manjaro-ARM' %}
{{ pillar[ polaris ] }}:
pkg.installed:
- name: {{ pillar[ polaris ] }}
- refresh: False
{% endif %}
/etc/rkhunter.d:
file.directory:
- makedirs: True
fix_executable:
file.managed:
- source:
- salt://app_rkhunter/files/rkhunter
- name: /usr/sbin/rkhunter
/etc/rkhunter.d/adore_kfd_whitelist.conf:
file.managed:
- source:
- salt://app_rkhunter/files/rkhunter.d/adore_kfd_whitelist.conf.{{ grains['id'] }}
- salt://app_rkhunter/files/rkhunter.d/adore_kfd_whitelist.conf.fallback
/etc/rkhunter.d/backup_enc.conf:
file.managed:
- source:
- salt://app_rkhunter/files/rkhunter.d/backup_enc.conf.{{ grains['id'] }}
- salt://app_rkhunter/files/rkhunter.d/backup_enc.conf.fallback
/etc/rkhunter.d/postgresql_dev.conf:
file.managed:
- source:
- salt://app_rkhunter/files/rkhunter.d/postgresql_dev.conf.{{ grains['id'] }}
- salt://app_rkhunter/files/rkhunter.d/postgresql_dev.conf.fallback
/etc/rkhunter.d/scriptwhitelist.conf:
file.managed:
- source:
- salt://app_rkhunter/files/rkhunter.d/scriptwhitelist.conf.{{ grains['id'] }}
- salt://app_rkhunter/files/rkhunter.d/scriptwhitelist.conf.fallback
/etc/rkhunter.d/systemd_hidden_update.conf:
file.managed:
- source:
- salt://app_rkhunter/files/rkhunter.d/systemd_hidden_update.conf.{{ grains['id'] }}
- salt://app_rkhunter/files/rkhunter.d/systemd_hidden_update.conf.fallback
/etc/rkhunter.d/ipc_shared_mem_whitelist.conf:
file.managed:
- source:
- salt://app_rkhunter/files/rkhunter.d/ipc_shared_mem_whitelist.conf.{{ grains['id'] }}
- salt://app_rkhunter/files/rkhunter.d/ipc_shared_mem_whitelist.conf.fallback
/etc/rkhunter.d/etc_hidden_java.conf:
file.managed:
- source:
- salt://app_rkhunter/files/rkhunter.d/etc_hidden_java.conf.{{ grains['id'] }}
- salt://app_rkhunter/files/rkhunter.d/etc_hidden_java.conf.fallback
{% endif %}The above state installs, creates configuration directory, poplulares with machine specific files ore a “fallback” config file if no machine specific file exists. The software package is installed, configured and updated by running:
sudo salt 'minion_name' state_apply app_rkhunter Usage
- After install, but before first check, rkhungter should have it’s properties updated as per installed configuration files, the command to do this while on a node itself is:
sudo rkhunter --propupd The output of the command should look something like this:
[ Rootkit Hunter version 1.4.6 ]
File updated: searched for 176 files, found 137
$- Before updating system check for changes. The command to do this is
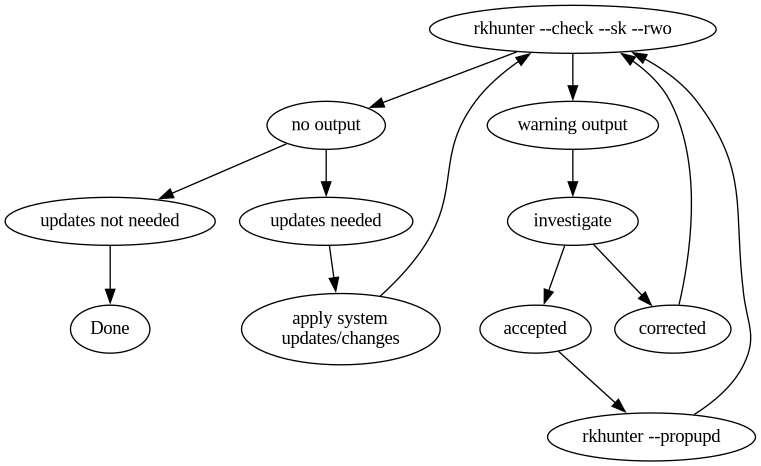
sudo rkhunter --check --sk --rwo The output of the command should look some thing like the following:
$–check directs checks be run against system, –sk tels program to skip pausing between checks, and –rwo tells the program to remain silent unless the checks identify something to warn about. If theire is no output from running the check, then the system is ready for whatever updates you need to apply. Once updates have neen applied, run the check command again and this time there could well be warnings in the outpot.
- All warnings should be investigated and corrected or if understood and required, whitelisted by adding to the configuration files. If the warnings are related to known changes or have been investigated nd eliminated, run the property update again to accept the new state of the system:
sudo rkhunter --propupd - As a final check, run the check command one more time and the output should come back empty.
My Rkhunter Work Flow